Vpn For Computer
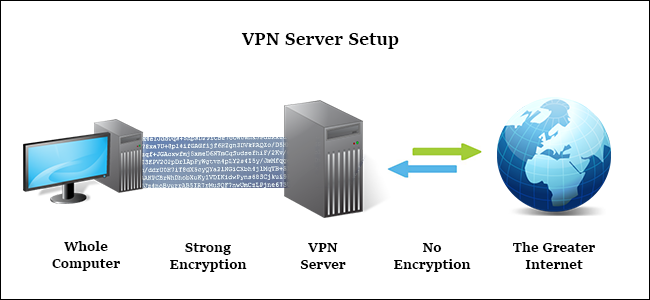
Sitetosite VPN A sitetosite VPN allows offices in multiple fixed locations to establish secure connections with each other. Learn how sitetosite VPNs works. A virtual private network is the best way to stay anonymous online and secure your web traffic. Weve tested more than 50 VPNs, and these are our top performers. Cyberstalking Suspect Arrested After VPN Providers Shared Logs With the FBIVPN providers often advertise their products as a method of surfing the web anonymously, claiming they never store logs of user activity, but a recent criminal case shows that at least some, do store user activity logs. The case in question is of Ryan Lin, a 2. Newton, Massachusetts, arrested on Thursday, October 5, on charges of cyberstalking. According to an FBI affidavit published by the US Department of Justice, Lin is accused of harassing and cyberstalking an unnamed 2. Jennifer Smith between April 2. It all started with a Craigslist ad. The two met after Lin answered a Craigslist ad and moved in with Smith and her two other roommates. The FBI says that soon after Lin moved in with Smith, she was the victim of multiple hacking, harassing, and cyberstalking incidents. Vpn For Computer' title='Vpn For Computer' />Investigators believe that Lin got access to passwords of some of Smiths online profiles because Smith didnt have a lock on her room door, and didnt password protect her computer. Authorities say that Lin allegedly accessed Smits Apple i. Cloud account from where he downloaded personal photos, and also her Google Drive account from where he took her private journal. Smith was the victim of a wide range of harassment campaigns. According to the affidavit, Lin is the prime suspect behind a multi faceted and unyielding harassment campaign that spanned months. In no particular order, below are some of the FBIs accusations The suspect allegedly created a collage of Smiths personal photos and non related sexually explicit images and sent it to Smiths friends, classmates, teachers, co workers, roommates, and family friends including a minor. The emails were spoofed to make them appear as coming from Smiths email address. The suspect allegedly sent excerpts of Smiths private journal to other persons, revealing personal details such as a past medical, psychological, and sexual history. The suspect allegedly created online accounts in Smiths name on adult portals asking people to show up at her house to enact BDSM, gangbang, rape, and other sexual fantasies. At least three people showed up. The suspect allegedly harrassed Smith using SMS messages sent via an anonymous text messaging service textnow. VPN Virtual Private Network technology lets a computer using a public Internet connection join a private network by way of a secure tunnel between that. You have a Windows 8. VPN software installed. When you upgrade this computer to Windows 10, it may no. A virtual private network VPN provides a secure, encrypted tunnel to transmit data between a remote user via the Internet and the company network. The suspect allegedly spoofed Smiths identity to send bomb and other threats to nearby schools and lone individuals. The suspect allegedly sent threatening communications to Smiths friends, associates, and family including a minor, urging Smith to commit suicide, or threatening to kill and rape Smith and associates. The suspect allegedly bombarded Smith with friend requests on Facebook, even after getting blocked. The suspect allegedly hacked Smith Rover. Smith intentionally killed one of their pets, resulting in the pet owners sending police officers to their house to deal with Smith. The suspect brought up the fact that Smith had an abortion, even if the suspect did not tell anyone about it, and only recorded the event in her private journal. Smith told authorities the abusive behavior began soon after Lin moved in, and continued even if she moved out two months later, scared by his actions. Lins abusive behavior was then redirected to the other two roommates, and following complaints to the landlord and police, Lin was kicked out from the shared apartment in August 2. The cyberstalking and harassing behavior continued, again, mainly directed at Smith. Suspect hid behind VPNs, Tor, Proton. Mail. For all of these actions, the suspect used Proton. Mail, VPN clients, and Tor to hide his identity. After local police investigated all the victims complaints for almost a year, they called in the FBI to help. The FBI found their first evidence at one of Lins former employers. The company had reinstalled Lins work computer after he left, but the FBI was able to find various artifacts in the hard drives unallocated disk space. Evidence includes Google Chrome artifacts that Lin had read about the bomb threats against local schools. Google Chrome artifacts that Lin had an account on textnow. Google Chrome artifacts that Lin had an account on Proton. Mail Google Chrome artifacts that Lin had visited Rover. Google Chrome artifacts that Lin had visited the Smiths Spotify profile, but also the profiles of Smiths brother and one of her best friends. Pure. VPN artifacts suggesting Lin was using the companys VPN client. VPN activity logs tie Lin to Smiths harassment. Yet, the most conclusive evidence came after the FBI managed to obtain logs from two VPN providers Pure. VPN and WANSecurity. The logs showed how within the span of minutes the same VPN IP address had logged into Lins real Gmail address, another Gmail address used for some of the threats, and a Rover. Lin created to discover Smiths real phone number. Pure. VPN was later able to link the stalking activity with Lins home and work IPs. Vpn For Computer' title='Vpn For Computer' />The information in the affidavit may shock some Pure. VPN customers, as the company boldly advertises on its privacy policy page that it does not keep any logs. Ironically, FBI agents also found tweets in which Lin was warning other users that VPN providers store activity logs, advice he didnt follow himself. Investigators became sure they identified the right man after they interviewed some of Lins past classmates, who recounted a similar pattern of harassment and cyberstalking from a man they described as a computer genius. As alleged, Mr. Lin orchestrated an extensive, multi faceted campaign of computer hacking and online harassment that caused a huge amount of angst, alarm, and unnecessary expenditure of limited law enforcement resources, said FBI Special Agent in Charge Shaw. This kind of behavior is not a prank, and it isnt harmless. He allegedly scared innocent people, and disrupted their daily lives, because he was blinded by his obsession, the agent added. No one should feel unsafe in their own home, school, or workplace, and the FBI and our law enforcement partners hope todays arrest will deter others from engaging in similar criminal conduct. How VPNs Work How. Stuff. Works. As a business grows, it might expand to multiple shops or offices across the country and around the world. To keep things running efficiently, the people working in those locations need a fast, secure and reliable way to share information across computer networks. In addition, traveling employees like salespeople need an equally secure and reliable way to connect to their businesss computer network from remote locations. Easeus Disk Copy Technician Edition 2.3.1. One popular technology to accomplish these goals is a VPN virtual private network. A VPN is a private network that uses a public network usually the Internet to connect remote sites or users together. The VPN uses virtual connections routed through the Internet from the businesss private network to the remote site or employee. By using a VPN, businesses ensure security anyone intercepting the encrypted data cant read it. VPN was not the first technology to make remote connections. Several years ago, the most common way to connect computers between multiple offices was by using a leased line. Leased lines, such as ISDN integrated services digital network, 1. Kbps, are private network connections that a telecommunications company could lease to its customers. Leased lines provided a company with a way to expand its private network beyond its immediate geographic area. These connections form a single wide area network WAN for the business. Though leased lines are reliable and secure, the leases are expensive, with costs rising as the distance between offices increases. Today, the Internet is more accessible than ever before, and Internet service providers ISPs continue to develop faster and more reliable services at lower costs than leased lines. To take advantage of this, most businesses have replaced leased lines with new technologies that use Internet connections without sacrificing performance and security. Businesses started by establishing intranets, which are private internal networks designed for use only by company employees. Intranets enabled distant colleagues to work together through technologies such as desktop sharing. By adding a VPN, a business can extend all its intranets resources to employees working from remote offices or their homes. This article describes VPN components, technologies, tunneling and security. First, lets explore an analogy that describes how a VPN compares to other networking options.