Pinnacle Studio Version 8
Windows 10 und Kompatibilitt der lteren Pinnacle Studio Versionen 1115. Aus aktuellem Anlass mchte ich an dieser Stelle auf ein KompatibilittsProblem von. Pinnacle Studio 20 Ultimate Crack Keygen Full Version Free Download. Pinnacle Studio Ultimate 20 Keygen. Pinnacle Studio Ultimate 20 Crack with Keygen is the world. Part Two of the Pinnacle Studio 21 review. A summary of the video editing tools available in Pinnacles video editing software. Pinnacle Studio Ultimate Download. Discount use coupon code 1. PINNSAVE to get 1. Pinnacle Studio Ultimate is a piece of software that provides users with the possibility to create high quality HD and 3. D videos and presentations effortlessly. The program allows users to take advantage of a broad range of tools and effects to build impressive, highly customized clips. With the help of this program, users can add various elements to their videos with simple drag and drop actions, courtesy of an integrated Storyboard mode, but they can also opt in for more precise edition capabilities, if they are experienced editors. Pinnacle Studio Ultimate comes with support for recording convert from the screen and adding it to videos, courtesy of Live Screen Capture, and also allows users to add voice over when performing this action. Pinnacle Studio Ultimate comes with over two thousand video effects, both 2. D and 3. D and makes it easy for users to add any of them to their clips. Moreover, it includes support for filters and transitions, for additional customization. With the help of this program, users can enjoy multi layer editing, which gives them the option to combine a large number of video and audio tracks when creating their clips. Users can also create custom soundtracks with the help of Score. Fitter. Pinnacle Studio Ultimate includes a series of presets and plugins that offer a multiple video personalization capabilities, including transitions, light flairs, rays, jitters, and scratches. The tool also offers the possibility to stabilize videos, swap colors in a scene remove imperfections, magnify a video segment, pixelation, and make various other adjustments as well. K Ultra HD capabilities have been included in Pinnacle Studio Ultimate as well, with XAVC S support and 4. K smart encoding. Additionally, the program allows users to create DVDs and Blu Ray discs from their videos, as well as to export them to various popular formats out there. System requirements. Intel Core i. 3 or AMD A4 3. GHz or higher. Intel Core i. GHz or higher required for AVCHD Intel Quick Sync Video support. Intel Core i. 7 or AMD Athlon A1. Multi camera. 4 GB of RAM or higher, 8GB highly recommended for Multi camera. Direct. X graphics device recommended. 610 650 votes Download Pinnacle Studio Free. Pinnacle Studio is a well known video editor capable of handling HD and 3D files. Download Pinnacle. HEVC H. 2. 65 support requires Windows 1. PC hardware or graphics card. Minimum 2. 56. MB VGA VRAM, 5. MB or higher recommended. Display resolution 1. Windows compatible sound card multi channel output required for surround preview8 GB HDD space for full installation. 
 Internet connection. Pinnacle Studio 2. Crack Plus Torrent is Free Download HerePinnacle Studio Crack 2. Plus is a powerful tool for nonlinear video editing and video tutorial editing and enhancing including HD quality, including Blu ray and AVCHD. With this program, you can create professional videos, and various results, transitions, and animations, overlay audio tracks there can be a possibility to add surround audio. Ready made jobs can be publicized on the You. Tube service or burn up it to Dvd videos and lightweight devices. The application form carries a variety of tools for creating game titles, announcer comments, light, color modification and special results. The capability to create your own soundtrack correctly matched up to the period of the video tutorial by using Smart. Sound. It helps you to sound reduction filtration system. In New Version result of the improved stereo system. Transfer of background may seem with MP3 data or straight from a music CD. The capability to track record your own narration. Pinnacle Studio Crack With Keygen Full Version Free Download. The most recent version brings about 1. D 3. D results, the capability to create stereoscopic 3. D films, enhance and retouch videos and photographs in the timeline, comprising six tracks. Better and faster transfer of recordings and photographs from cellular devices. Furthermore, it includes added the capability to merge Dolby Digital 5. Blu ray discs. Whats New in Pinnacle Studio 2. Capture and edit in widescreen 1. Capture DV digital content directly to MPEG 2 with DVD quality and later edit them. Full screen video preview. Wide angle lens correction. XAVC S support. Full Screen recording software. Pro level audio tools. New Version Pinnacle Studio 2. Main Features Enjoy with a freeze frame for creating brilliant animation effects. The capability to apply various results and animation when making a video. The occurrence of a distinctive image stabilization technology, commonly found in movies. Capability to create game titles, announcer comments, Dvd movie menus using results and web templates more than 8. Capability to post videos to You. Tube. Pinnacle Studio 2. Torrent Free Download Here Now. Burn Dvd and Blu ray HD Movie, Blu ray Disc plus much more. Import MP3 audio tracks or immediately from audio tracks CDs. Possibility to track record your own narration. Noise reduction filtration. Extended stereo result. Widescreen Surround Audio. How to Crack Pinnacle Studio 2. First of all, Download Cracked File Below. Extract this File and Run it. Click on Pathed button. Wait for a mint. After that Click in Active it Button. Thats All Done. Here.
Internet connection. Pinnacle Studio 2. Crack Plus Torrent is Free Download HerePinnacle Studio Crack 2. Plus is a powerful tool for nonlinear video editing and video tutorial editing and enhancing including HD quality, including Blu ray and AVCHD. With this program, you can create professional videos, and various results, transitions, and animations, overlay audio tracks there can be a possibility to add surround audio. Ready made jobs can be publicized on the You. Tube service or burn up it to Dvd videos and lightweight devices. The application form carries a variety of tools for creating game titles, announcer comments, light, color modification and special results. The capability to create your own soundtrack correctly matched up to the period of the video tutorial by using Smart. Sound. It helps you to sound reduction filtration system. In New Version result of the improved stereo system. Transfer of background may seem with MP3 data or straight from a music CD. The capability to track record your own narration. Pinnacle Studio Crack With Keygen Full Version Free Download. The most recent version brings about 1. D 3. D results, the capability to create stereoscopic 3. D films, enhance and retouch videos and photographs in the timeline, comprising six tracks. Better and faster transfer of recordings and photographs from cellular devices. Furthermore, it includes added the capability to merge Dolby Digital 5. Blu ray discs. Whats New in Pinnacle Studio 2. Capture and edit in widescreen 1. Capture DV digital content directly to MPEG 2 with DVD quality and later edit them. Full screen video preview. Wide angle lens correction. XAVC S support. Full Screen recording software. Pro level audio tools. New Version Pinnacle Studio 2. Main Features Enjoy with a freeze frame for creating brilliant animation effects. The capability to apply various results and animation when making a video. The occurrence of a distinctive image stabilization technology, commonly found in movies. Capability to create game titles, announcer comments, Dvd movie menus using results and web templates more than 8. Capability to post videos to You. Tube. Pinnacle Studio 2. Torrent Free Download Here Now. Burn Dvd and Blu ray HD Movie, Blu ray Disc plus much more. Import MP3 audio tracks or immediately from audio tracks CDs. Possibility to track record your own narration. Noise reduction filtration. Extended stereo result. Widescreen Surround Audio. How to Crack Pinnacle Studio 2. First of all, Download Cracked File Below. Extract this File and Run it. Click on Pathed button. Wait for a mint. After that Click in Active it Button. Thats All Done. Here.
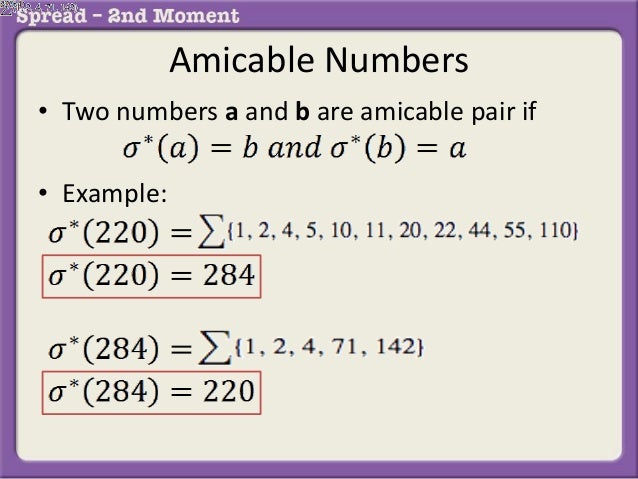
Amicable Numbers Program

Bell number Wikipedia. In combinatorial mathematics, the Bell numbers count the possible partitions of a set. These numbers have been studied by mathematicians since the 1. Japan, but they are named after Eric Temple Bell, who wrote about them in the 1. Starting with B0 B1 1, the first few Bell numbers are 1, 1, 2, 5, 1. A0. 00. 11. 0 in the OEIS. The nth of these numbers, Bn, counts the number of different ways to partition a set that has exactly n elements, or equivalently, the number of equivalence relations on it. Various Number Theorists Home PagesDepartmental listings Complete listing A B C D E F G H I J K L M N O P Q R S T U V. TeachWithMovies. org Create Lesson Plans from 425 Movies and Film Clips, Contact, Space Travel, Science Fiction. Mr. author infact 1,2,3,4,5,6,7,8,9 is also an armstrong number but your program doesnt display those so plz do the necessary. Outside of mathematics, the same number also counts the number of different rhyme schemes for n line poems. As well as appearing in counting problems, these numbers have a different interpretation, as moments of probability distributions. In particular, Bn is the nth moment of a Poisson distribution with mean 1. CountingeditSet partitionsedit. Partitions of sets can be arranged in a partial order, showing that each partition of a set of size n uses one of the partitions of a set of size n 1. The 5. 2 partitions of a set with 5 elements. In general, Bn is the number of partitions of a set of size n. A partition of a set S is defined as a set of nonempty, pairwise disjoint subsets of S whose union is S. For example, B3 5 because the 3 element set a, b, c can be partitioned in 5 distinct ways a, b, c a, b, c b, a, c c, a, b a, b, c. B0 is 1 because there is exactly one partition of the empty set. Every member of the empty set is a nonempty set that is vacuously true, and their union is the empty set. Therefore, the empty set is the only partition of itself. As suggested by the set notation above, we consider neither the order of the partitions nor the order of elements within each partition. This means that the following partitionings are all considered identical b, a, c a, c, b b, c, a c, a, b. If, instead, different orderings of the sets are considered to be different partitions, then the number of these ordered partitions is given by the ordered Bell numbers. FactorizationseditIf a number N is a squarefree positive integer meaning that it is the product of some number n of distinct prime numbers, then Bn gives the number of different multiplicative partitions of N. These are factorizations of N into numbers greater than one, treating two factorizations as the same if they have the same factors in a different order. 2 For instance, 3. B3 5 factorizations 3. A software platform for distributed computing using volunteer computer resources. Descriptions of areascourses in number theory. Mathematics Subject Classification, 11XX Eric Weissteins World of Mathematics Number Theory section. Rhyme schemeseditThe Bell numbers also count the rhyme schemes of an n line poem or stanza. A rhyme scheme describes which lines rhyme with each other, and so may be interpreted as a partition of the set of lines into rhyming subsets. Rhyme schemes are usually written as a sequence of Roman letters, one per line, with rhyming lines given the same letter as each other, and with the first lines in each rhyming set labeled in alphabetical order. Thus, the 1. 5 possible four line rhyme schemes are AAAA, AAAB, AABA, AABB, AABC, ABAA, ABAB, ABAC, ABBA, ABBB, ABBC, ABCA, ABCB, ABCC, and ABCD. PermutationseditThe Bell numbers come up in a card shuffling problem mentioned in the addendum to Gardner 1. If a deck of n cards is shuffled by repeatedly removing the top card and reinserting it anywhere in the deck including its original position at the top of the deck, with exactly n repetitions of this operation, then there are nn different shuffles that can be performed. Of these, the number that return the deck to its original sorted order is exactly Bn. Thus, the probability that the deck is in its original order after shuffling it in this way is Bnnn, which is significantly larger than the 1n Related to card shuffling are several other problems of counting special kinds of permutations that are also answered by the Bell numbers. For instance, the nth Bell number equals number of permutations on n items in which no three values that are in sorted order have the last two of these three consecutive. In a notation for generalized permutation patterns where values that must be consecutive are written adjacent to each other, and values that can appear non consecutively are separated by a dash, these permutations can be described as the permutations that avoid the pattern 1 2. The permutations that avoid the generalized patterns 1. Bell numbers. The permutations in which every 3. Bell numbers. However, the Bell numbers grow too quickly to count the permutations that avoid a pattern that has not been generalized in this way by the now proven StanleyWilf conjecture, the number of such permutations is singly exponential, and the Bell numbers have a higher asymptotic growth rate than that. Triangle scheme for calculationsedit. The triangular array whose right hand diagonal sequence consists of Bell numbers. 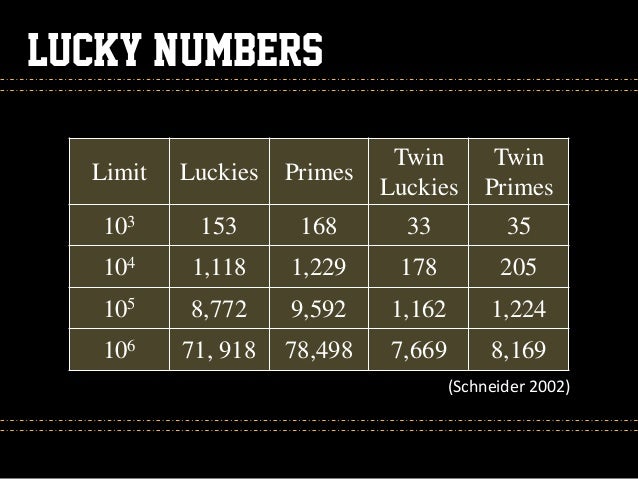
 The Bell numbers can easily be calculated by creating the so called Bell triangle, also called Aitkens array or the Peirce triangle after Alexander Aitken and Charles Sanders Peirce. 5Start with the number one. Put this on a row by itself. Start a new row with the rightmost element from the previous row as the leftmost number xi,1xi1,rdisplaystyle xi,1leftarrow xi 1,r where r is the last element of i 1 th rowDetermine the numbers not on the left column by taking the sum of the number to the left and the number above the number to the left, that is, the number diagonally up and left of the number we are calculating xi,jxi,j1xi1,j1displaystyle xi,jleftarrow xi,j 1xi 1,j 1Repeat step three until there is a new row with one more number than the previous row Do Step 3 until jr1displaystyle jr1The number on the left hand side of a given row is the Bell number for that row. Bixi,1displaystyle Bileftarrow xi,1Here are the first five rows of the triangle constructed by these rules. The Bell numbers appear on both the left and right sides of the triangle. PropertieseditSummation formulaseditThe Bell numbers satisfy a recurrence relation involving binomial coefficients Bn1k0nnkBk. displaystyle Bn1sum k0nbinom nkBk. It can be explained by observing that, from an arbitrary partition of n 1 items, removing the set containing the first item leaves a partition of a smaller set of k items for some number k that may range from 0 to n. There are nkdisplaystyle tbinom nk choices for the k items that remain after one set is removed, and Bk choices of how to partition them. A different summation formula represents each Bell number as a sum of Stirling numbers of the second kind. Bnk0nnk. displaystyle Bnsum k0nleftn atop kright. The Stirling number nkdisplaystyle leftn atop kright is the number of ways to partition a set of cardinality n into exactly k nonempty subsets. Thus, in the equation relating the Bell numbers to the Stirling numbers, each partition counted on the left hand side of the equation is counted in exactly one of the terms of the sum on the right hand side, the one for which k is the number of sets in the partition. Spivey 2. 00. 8 has given a formula that combines both of these summations Bnmk0nj0mmjnkjnk. Bk. displaystyle Bnmsum k0nsum j0mleftm atop jrightn choose kjn kBk. Generating functioneditThe exponential generating function of the Bell numbers is. DESCRIPTIONS OF AREASCOURSES IN NUMBER THEORYThe ABC Conjecture. New Scientist article on the ABC conjecture. Notes on the Oxford IUT workshop by Brian Conrad. An ABC proof too tough even for mathematicians, Kevin Hartnett Boston Globe, November 4, 2. The abc conjecture, as easy as 1, 2, 3 or not, Alex Ghitza, The Conversation, 2. November 2. 01. 2. The ABCs of Number Theory Noam Elkies. Reken mee met ABC Bart de Smit, Gillien Geuze, Nieuw Archief voor Wiskunde 5th series 8 2. Reken Mee met ABCThe ABC conjecture, Frits Beukers, ABC day, Leiden, September 9, 2. ABChome finding abc triples related to the ABC conjecture. Special day on the ABC conjecture, Intercity Number Theory Seminar, September 9th 2. Its As Easy As abc, Andrew Granville and Thomas J. Tucker, AMS Notices, November 2. The ABC Conjecture Home Page Abderrahmane Nitaj. Arithmetical Geometry. Langlands Program, trace formulas, and their geometrization, Edward Frenkel, Bull. Amer. Math. Soc. October 1. Arithmetic on curves, Barry Mazur, Bull. Amer. Math. Soc. 1. The l adic revolution in number theory, a video of a talk by Nick Katz at the IHES Colloquium in honour of Alexander Grothendieck, January 1. Conferences in Arithmetic Geometry Kiran Kedlaya. Videos of lectures, Clay Mathematics Institute 2. Summer School on Arithmetic Geometry, July 1. August 1. 1, 2. 00. Mathematisches Institut, Georg August Universitt, Gttingen. Topics in Arithmetical Geometry Outline of a course by Shou Wu Zhang pdf. Grothendiecks SGALecture notes on the local Langlands correspondence Michael Harris. Modular Mahler Measures, slides by Fernando Villegas. Diophantine geometry in characteristic p a survey, Felipe Voloch. Draft of PCMI Lecture Notes on Open Questions in Arithmetic Algebraic Geometry Alice Silverberg ps file 8. K. Fermats Last Theorem. The generalized Fermat equation Frits Beukers. Fermats Last Theorem Wikibooks. The proof of Fermats Last Theorem by R. Taylor and A. Wiles, Gerd Faltings, Notices of the AMS, 4. July 1. 99. 5. Beals conjecture. A proof of the full Shimura Taniyama Weil conjecture is announced, Henri Darmon, Notices of the AMS, December 1. A report on Wiles Cambridge lectures, K. Rubin, A. Silverberg, Bull. Amer. Math. Soc. 3. William Hammonds Fermat Archive. Charles Daneys pages on Fermats last Theorem. Notes on Fermats Last Theorem, A. J. van der Poorten, Canadian Mathematical Society Series of Monographs and Advanced Texts, Wiley Interscience, January, 1. ISBN 0 4. 71 0. The Solving of Fermats Last Theorem, Karl Rubin, Ohio State University Distinguished Lecture May 2. Le Thorme de Fermat Karim Belabas and Catherine Goldstein. Irregular primes. Pell equations. Michel Waldschmidts lecture notes on Lquation dite de Pell Fermat and quations Diophantiennes. Pell equation bibliography, 1. Franz Lemmermeyer. Linear Recurrences for Pell Equations John Robertson. A Fast Algorithm for Computing the Regulator of an Order of a Real Quadratic Field John Robertson. Strmers theorem. BCMATH program for solving x. Lagrange Mollin Matthews method Keith Matthews. Pells equation Andrej Nowicki. Pells equation Mac. Tutor History of Mathematics Archive. Record Holder Solutions of Pells Equation Toms Oliveira e Silva. Solving the Pell equation, H. W. Lenstra Jr., Notices of the AMS, February 2. Solving the equation ax. John Robertson. Solving the generalised Pell equation x. N John Robertson. BCMATH Pell equation program Keith Matthews. BCMATH program of the Grytczuk, Luca, Wojtowicz GLW construction of non square d 0, for which x. Keith Matthews. Primes and factoring. Fourier Series for Prime Counting Functions. Mathematicians Discover Prime Conspiracy. Andricas conjecture. Prime Numbers A Much Needed Gap Is Finally Found, John Friedlander, AMS Notices, June July 2. Polymath article on recent advances in the study of prime numbers. Primes in intervals of bounded length, Andrew Granville, Bull. Amer. Math. Soc. 5. Primo, a primality proving program based on the ECPP algorithm Marcel Martin. Problems on combinatorial properties of primes Zhi Wei Sun. Super Twin Prime Conjecture, a message to the Number Theory List, Feb. Zhi Wei Sun. Unification of Goldbachs conjecture and the twin prime conjecture, a message to Number Theory List, January 2. Zhi Wei Sun. Factorizations of bn1, b2,3,5,6,7,1. Up to High Powers, third Edition, free download from AMS. Progress made on de Polignacs conjecture. Conjectures involving primes and quadratic forms, Zhi Wei Sun. Firoozbakhts conjecture. Slide talk by Jonathan Sondow Lerch quotients and primes, Fermat Wilson quotients, and the Wieferich non Wilson prime 1. Gelfonds power tower conjecture. Landaus problems on primes Jnos Pintz. Expository article on the recent theorem of Goldston, Pintz, and Yildirim on small gaps between prime numbers, K. Soundararajan. The Challenge of Large Numbers Richard Crandall. The ECMNET Project Small gaps between prime numbers The work of Goldston Pintz Yildirim, K. Soundararajan, Bulletin Amer. Math. Soc. 4. 4 2. Small gaps between primes, transparencies of a talk by Jimena Sivak Fischler. Prime constellation records Jens Kruse Andersen. Primzahlbeweise. Primes of the form x. Marios Magioladitis. The Green Tao Theorem on arithmetic progressions in the primes an ergodic point of view, Bryna Kra, Bull. Amer. Math. Soc. 4. About the cover On the distribution of primes Gauss tables, Yuri Tschinkel, Bull. Amer. Math. Soc. 4. The Niven Lectures, Carl Pomerance March 2. University of British Columbia. It is easy to determine whether a given integer is prime, Andrew Granville, Bull. Amer. Math. Soc. 4. Generalized Fermat Primes Search. PRIMES is in P a non specialist account by Folkmar Bornemann. Exposition of the Primes is in P theorem Kevin Ford. Review of Prime numbers A computational perspective, Reviewer Jeremy Teitelbaum. The Prime Pages. The Nth prime page. Largest Known Primes. Mersenne Primes History, Theorems and Lists. Mac. Tutor History of Mathematics Prime Numbers. Mersenne Prime Search. Gordon Spences Mersenne prime discovery. Will Edgingtons Mersenne Primes Page. AMS Notices article on Primality Testing Richard Pinch. Frobenius Pseudoprimes Jon Grantham. Appendix 1 Factorization results Hisanori Mishima. Factorizations of Cyclotomic Numbers Mitsuo Morimoto. Factorization of Generalized Repunits Andy Steward. All known factors of 3. Pollards p 1 method Andy Steward. Repunit primes and factors of 1. Torbjrn Granlund. Surprising connections between prime numbers and physics Matthew Watkins. Lucas Lehmer criterion Paul Garrett. Lucas Lehmer test for Mersenne numbers Wikipedia. Factorizations of xy yx for 1 lt y lt x lt 1. Andrey Kulsha. Arithmetic Progression of 2. Prime number theorem. Complex Variables, by Robert Ash and W. P. Novinger has a chapter on the prime number theorem. Prime gaps. Sums of integer cubes. Table of non negative integral solutions of nx. Hisanori Mishima. Twin primes. Elliptic Curves. Rational points on, and the arithmetic of, elliptic curves A tale of two books and an article, J. H. Silverman, Bull. Amer. Math. Soc. January 5, 2. How many rational points does a random curve have, Wei Ho, Bull. Amer. Math. Soc. 5. Sage Days 2. 2 Computing with Elliptic Curves. Topics in Algebraic Geometry Elliptic Curves, Lecture course by Franz Lemmermeyer. Lang Trotter revisited, Nicholas M. Katz, Bull. Amer. Math. Soc. 4. 6 2.
The Bell numbers can easily be calculated by creating the so called Bell triangle, also called Aitkens array or the Peirce triangle after Alexander Aitken and Charles Sanders Peirce. 5Start with the number one. Put this on a row by itself. Start a new row with the rightmost element from the previous row as the leftmost number xi,1xi1,rdisplaystyle xi,1leftarrow xi 1,r where r is the last element of i 1 th rowDetermine the numbers not on the left column by taking the sum of the number to the left and the number above the number to the left, that is, the number diagonally up and left of the number we are calculating xi,jxi,j1xi1,j1displaystyle xi,jleftarrow xi,j 1xi 1,j 1Repeat step three until there is a new row with one more number than the previous row Do Step 3 until jr1displaystyle jr1The number on the left hand side of a given row is the Bell number for that row. Bixi,1displaystyle Bileftarrow xi,1Here are the first five rows of the triangle constructed by these rules. The Bell numbers appear on both the left and right sides of the triangle. PropertieseditSummation formulaseditThe Bell numbers satisfy a recurrence relation involving binomial coefficients Bn1k0nnkBk. displaystyle Bn1sum k0nbinom nkBk. It can be explained by observing that, from an arbitrary partition of n 1 items, removing the set containing the first item leaves a partition of a smaller set of k items for some number k that may range from 0 to n. There are nkdisplaystyle tbinom nk choices for the k items that remain after one set is removed, and Bk choices of how to partition them. A different summation formula represents each Bell number as a sum of Stirling numbers of the second kind. Bnk0nnk. displaystyle Bnsum k0nleftn atop kright. The Stirling number nkdisplaystyle leftn atop kright is the number of ways to partition a set of cardinality n into exactly k nonempty subsets. Thus, in the equation relating the Bell numbers to the Stirling numbers, each partition counted on the left hand side of the equation is counted in exactly one of the terms of the sum on the right hand side, the one for which k is the number of sets in the partition. Spivey 2. 00. 8 has given a formula that combines both of these summations Bnmk0nj0mmjnkjnk. Bk. displaystyle Bnmsum k0nsum j0mleftm atop jrightn choose kjn kBk. Generating functioneditThe exponential generating function of the Bell numbers is. DESCRIPTIONS OF AREASCOURSES IN NUMBER THEORYThe ABC Conjecture. New Scientist article on the ABC conjecture. Notes on the Oxford IUT workshop by Brian Conrad. An ABC proof too tough even for mathematicians, Kevin Hartnett Boston Globe, November 4, 2. The abc conjecture, as easy as 1, 2, 3 or not, Alex Ghitza, The Conversation, 2. November 2. 01. 2. The ABCs of Number Theory Noam Elkies. Reken mee met ABC Bart de Smit, Gillien Geuze, Nieuw Archief voor Wiskunde 5th series 8 2. Reken Mee met ABCThe ABC conjecture, Frits Beukers, ABC day, Leiden, September 9, 2. ABChome finding abc triples related to the ABC conjecture. Special day on the ABC conjecture, Intercity Number Theory Seminar, September 9th 2. Its As Easy As abc, Andrew Granville and Thomas J. Tucker, AMS Notices, November 2. The ABC Conjecture Home Page Abderrahmane Nitaj. Arithmetical Geometry. Langlands Program, trace formulas, and their geometrization, Edward Frenkel, Bull. Amer. Math. Soc. October 1. Arithmetic on curves, Barry Mazur, Bull. Amer. Math. Soc. 1. The l adic revolution in number theory, a video of a talk by Nick Katz at the IHES Colloquium in honour of Alexander Grothendieck, January 1. Conferences in Arithmetic Geometry Kiran Kedlaya. Videos of lectures, Clay Mathematics Institute 2. Summer School on Arithmetic Geometry, July 1. August 1. 1, 2. 00. Mathematisches Institut, Georg August Universitt, Gttingen. Topics in Arithmetical Geometry Outline of a course by Shou Wu Zhang pdf. Grothendiecks SGALecture notes on the local Langlands correspondence Michael Harris. Modular Mahler Measures, slides by Fernando Villegas. Diophantine geometry in characteristic p a survey, Felipe Voloch. Draft of PCMI Lecture Notes on Open Questions in Arithmetic Algebraic Geometry Alice Silverberg ps file 8. K. Fermats Last Theorem. The generalized Fermat equation Frits Beukers. Fermats Last Theorem Wikibooks. The proof of Fermats Last Theorem by R. Taylor and A. Wiles, Gerd Faltings, Notices of the AMS, 4. July 1. 99. 5. Beals conjecture. A proof of the full Shimura Taniyama Weil conjecture is announced, Henri Darmon, Notices of the AMS, December 1. A report on Wiles Cambridge lectures, K. Rubin, A. Silverberg, Bull. Amer. Math. Soc. 3. William Hammonds Fermat Archive. Charles Daneys pages on Fermats last Theorem. Notes on Fermats Last Theorem, A. J. van der Poorten, Canadian Mathematical Society Series of Monographs and Advanced Texts, Wiley Interscience, January, 1. ISBN 0 4. 71 0. The Solving of Fermats Last Theorem, Karl Rubin, Ohio State University Distinguished Lecture May 2. Le Thorme de Fermat Karim Belabas and Catherine Goldstein. Irregular primes. Pell equations. Michel Waldschmidts lecture notes on Lquation dite de Pell Fermat and quations Diophantiennes. Pell equation bibliography, 1. Franz Lemmermeyer. Linear Recurrences for Pell Equations John Robertson. A Fast Algorithm for Computing the Regulator of an Order of a Real Quadratic Field John Robertson. Strmers theorem. BCMATH program for solving x. Lagrange Mollin Matthews method Keith Matthews. Pells equation Andrej Nowicki. Pells equation Mac. Tutor History of Mathematics Archive. Record Holder Solutions of Pells Equation Toms Oliveira e Silva. Solving the Pell equation, H. W. Lenstra Jr., Notices of the AMS, February 2. Solving the equation ax. John Robertson. Solving the generalised Pell equation x. N John Robertson. BCMATH Pell equation program Keith Matthews. BCMATH program of the Grytczuk, Luca, Wojtowicz GLW construction of non square d 0, for which x. Keith Matthews. Primes and factoring. Fourier Series for Prime Counting Functions. Mathematicians Discover Prime Conspiracy. Andricas conjecture. Prime Numbers A Much Needed Gap Is Finally Found, John Friedlander, AMS Notices, June July 2. Polymath article on recent advances in the study of prime numbers. Primes in intervals of bounded length, Andrew Granville, Bull. Amer. Math. Soc. 5. Primo, a primality proving program based on the ECPP algorithm Marcel Martin. Problems on combinatorial properties of primes Zhi Wei Sun. Super Twin Prime Conjecture, a message to the Number Theory List, Feb. Zhi Wei Sun. Unification of Goldbachs conjecture and the twin prime conjecture, a message to Number Theory List, January 2. Zhi Wei Sun. Factorizations of bn1, b2,3,5,6,7,1. Up to High Powers, third Edition, free download from AMS. Progress made on de Polignacs conjecture. Conjectures involving primes and quadratic forms, Zhi Wei Sun. Firoozbakhts conjecture. Slide talk by Jonathan Sondow Lerch quotients and primes, Fermat Wilson quotients, and the Wieferich non Wilson prime 1. Gelfonds power tower conjecture. Landaus problems on primes Jnos Pintz. Expository article on the recent theorem of Goldston, Pintz, and Yildirim on small gaps between prime numbers, K. Soundararajan. The Challenge of Large Numbers Richard Crandall. The ECMNET Project Small gaps between prime numbers The work of Goldston Pintz Yildirim, K. Soundararajan, Bulletin Amer. Math. Soc. 4. 4 2. Small gaps between primes, transparencies of a talk by Jimena Sivak Fischler. Prime constellation records Jens Kruse Andersen. Primzahlbeweise. Primes of the form x. Marios Magioladitis. The Green Tao Theorem on arithmetic progressions in the primes an ergodic point of view, Bryna Kra, Bull. Amer. Math. Soc. 4. About the cover On the distribution of primes Gauss tables, Yuri Tschinkel, Bull. Amer. Math. Soc. 4. The Niven Lectures, Carl Pomerance March 2. University of British Columbia. It is easy to determine whether a given integer is prime, Andrew Granville, Bull. Amer. Math. Soc. 4. Generalized Fermat Primes Search. PRIMES is in P a non specialist account by Folkmar Bornemann. Exposition of the Primes is in P theorem Kevin Ford. Review of Prime numbers A computational perspective, Reviewer Jeremy Teitelbaum. The Prime Pages. The Nth prime page. Largest Known Primes. Mersenne Primes History, Theorems and Lists. Mac. Tutor History of Mathematics Prime Numbers. Mersenne Prime Search. Gordon Spences Mersenne prime discovery. Will Edgingtons Mersenne Primes Page. AMS Notices article on Primality Testing Richard Pinch. Frobenius Pseudoprimes Jon Grantham. Appendix 1 Factorization results Hisanori Mishima. Factorizations of Cyclotomic Numbers Mitsuo Morimoto. Factorization of Generalized Repunits Andy Steward. All known factors of 3. Pollards p 1 method Andy Steward. Repunit primes and factors of 1. Torbjrn Granlund. Surprising connections between prime numbers and physics Matthew Watkins. Lucas Lehmer criterion Paul Garrett. Lucas Lehmer test for Mersenne numbers Wikipedia. Factorizations of xy yx for 1 lt y lt x lt 1. Andrey Kulsha. Arithmetic Progression of 2. Prime number theorem. Complex Variables, by Robert Ash and W. P. Novinger has a chapter on the prime number theorem. Prime gaps. Sums of integer cubes. Table of non negative integral solutions of nx. Hisanori Mishima. Twin primes. Elliptic Curves. Rational points on, and the arithmetic of, elliptic curves A tale of two books and an article, J. H. Silverman, Bull. Amer. Math. Soc. January 5, 2. How many rational points does a random curve have, Wei Ho, Bull. Amer. Math. Soc. 5. Sage Days 2. 2 Computing with Elliptic Curves. Topics in Algebraic Geometry Elliptic Curves, Lecture course by Franz Lemmermeyer. Lang Trotter revisited, Nicholas M. Katz, Bull. Amer. Math. Soc. 4. 6 2.
Tyler Perry The Marriage Counselor Play

Xfinity. Now connecting to your entertainment experience. Biography. com shows how writer, actor, producer, and director Tyler Perry built an entertainment empire of successful films, plays, and a bestselling book. I really enjoyed revisiting lots of memories on your WAKY web site. I was privileged to do 700 PM to Midnights in 1958 1959. Tyler Perry Celebrity Profile Check out the latest Tyler Perry photo gallery, biography, pics, pictures, interviews, news, forums and blogs at Rotten TomatoesSYNOPSIS A bold exploration of the intrigue and perils of infidelity, Tyler Perrys Temptation Confessions of a Marriage Counselor is a compelling love story that. Directed by Tyler Perry. With Jurnee SmollettBell, Vanessa Williams, Brandy Norwood, Kim Kardashian West. An ambitious married womans temptation by a handsome. An explosive romance about forbidden desires, TYLER PERRYS TEMPTATION tells the provocative story of Judith, an ambitious married woman whose temptation. Enjoy Tyler Perrys The Marriage Counselor The Play online with XFINITYs highquality streaming anytime, anywhere. Watch your favorite movies with XFINITY today Tyler Perry Studios TPS is an American film production studio, founded by actor, filmmaker, and playwright Tyler Perry in 2006 in Atlanta, Georgia. Tyler Perrys The Marriage Counselor transforms the art of marriagelifeand family with this fun and fulfilling onstage experience. Tickets for Concerts, Sports, Theatre and More Online at TicketsInventory. com.
Tyler Perry Studios TPS is an American film production studio, founded by actor, filmmaker, and playwright Tyler Perry in 2006 in Atlanta, Georgia. Tyler Perrys The Marriage Counselor transforms the art of marriagelifeand family with this fun and fulfilling onstage experience. Tickets for Concerts, Sports, Theatre and More Online at TicketsInventory. com.
Pes 2013 Ultimate Editor
Update PES 2018 Professionals Patch v1 telah dirilis dengan berbagai fitur keren agar menunjang permainan PES 2018 menjadi semakin up to date PES 2013 Pro Evolution Soccer 2013 Demo . Daemon Tools Pro Final Full Crack sebuah software emulator CDDVD yang dapat anda gunakan untuk membuat virtual disk di komputer atau. PES 2. 01. 3. PES 2. 01. 3 Pro Evolution Soccer 2. Demo. . PES . PES Pro Evolution Soccer 1. Play Station. PC . PES 2. 01. 2 PES 2. Pro Evolution Soccer 2. Demo PES 2. PES 2. 01. 3 . XP Seven Vista 2. PES 2. 01. 3 PES 2. C Program FilesKONAMIPro Evolution Soccer 2. DEMO pes. PES 2. 01. 3 PES 2. 01. 3. 4. Doge Know Your Meme. About. Doge is a slang term for dog that is primarily associated with pictures of Shiba Inus nicknamed Shibe and internal monologue captions on Tumblr. These photos may be photoshopped to change the dogs face or captioned with interior monologues in Comic Sans font. Origin. The use of the misspelled word doge to refer to a dog dates back to June 2. Homestar Runners puppet show. In the episode titled Biz Cas Fri 1, Homestar calls Strong Bad his d o g e while trying to distract him from his work. Enjoy the videos and music you love, upload original content, and share it all with friends, family, and the world on YouTube. Doge is a slang term for dog that is primarily associated with pictures of Shiba Inus nicknamed Shibe and internal monologue captions on Tumblr. These. BAGAS31. com Pro Evolution Soccer PES 2018 memang sedang hangathangatnya dibicarakan. PES 2018 merupakan seri terbaru dari KONAMI yang baru rilis tahun ini. Identity. On February 2. Japanese kindergarten teacher Atsuko Sato posted several photos of her rescue adopted Shiba Inu dog Kabosu to her personal blog. September 27, 2013. NEWS. 3. stanger. WEEKLY. ZULU EDITOR Guy Vezi 0. REPORTER Jyothi Laldas 0. REPORTER Mervyn Krishna 0. YOUR. Tutte le risorse e download per Android apk Italia. PES 2013 PES Space Patch, Download PES 2013 PES Space Patch, Free PES 2013 PES Space Patch, PES 2013 PES Space Patch Full Version, PES 2013 PES Space Patch Single. Among the photos included a peculiar shot of Kabosu sitting on a couch while glaring sideways at the camera with raised eyebrows shown below, right. In December 2. 01. Doge, the tech news site The Verge published an article identifying Satos Kabosu as the original Shiba Inu depicted in the meme. In addition to Kabosu, The Verge also identified Suki, a Shiba Inu who lives with San Francisco based photographer Jonathan Fleming, as the scarfed dog portrayed in another popular instance of the meme. Spread. On October 2. Kabosu was submitted to the rAds subreddit with the title LMBOLOOK THISFUKKINDOGE, where it received 2. Sometime in April 2. Tumblr user leonsumbitches uploaded an audio file of a computer reading a passage written like the commands of a turn based adventure game about encountering a doge. The passage was paired with a photo of a woman patting a dog on the head and has gained more than 3. July 2. 01. 3. In response, the single topic blog Your Daily Doge was created, but was quickly abandoned after reblogging leonsumbitches post several times. On May 7th, You. Tuber Kwandao. Ren. 66 uploaded a video with a person reading the text over a fake Pokemon battle. By June, doge threads in which numerous people shared photos of dogs in different outfits began appearing on 4chan boards, including v Video Games. The same month, a photoset of a dog with a cup and saucer balanced on his head went viral on Tumblr after airpi referred to it as Polite Doge. In August, the first doge single topic blog, Fuck Yeah Doge, launched on Tumblr. The growth in summer 2. Tumblr Shiba Confessions, as people began to refer to these dogs as shibes. In December 2. Reddit in a post submitted to rDogs. IWanna. Hug. The same month, an interior monologue captioned photo of a Schnauzer was submitted to Cheezburger with the title Schnauze. On January 8th, 2. Doge was created, sharing photos and videos of the captioned Shiba Inus. In May, rdailydoge was created to share one dog photo a day, captioned or not. Another single topic blog, shibe doge, launched in July 2. Shiba Inu photos. On July 2. 9th, 2. Shit 4chan Says, garnering more than 6. On November 2. 0, 2. Youtube implemented an Easter egg, that changes the text to be colored and in Comic Sans, much like the original internal monologue style captions, when user searches the phrase doge meme. On Tumblr, in addition to the captioned photos, the doge tag often contains images of a Shiba Inu whose facial features have been manipulated, similar to Starecat. Murica Raid. On the evening of August 2. Reddits tongue in cheek patriotic forum rMurica, flooding the subreddits frontpage with dozens of photoshopped images depicting the Doge character in All American themed settings shown below. According to The Daily Dots report, the raid started late Sunday night and lasted until about 1. ET on August 2. 7th, at which point rMuricas moderators began removing Doge related posts from the subreddit index. Unlike previous clashes between the users of 4chan and Reddit, the sudden influx of Doge images was reportedly met by little opposition from Reddits userbase, reflecting the growing popularity of the character outside of Tumblr. Trademark Controversy. On June 2. 4th, 2. California based gaming accessory company filed to trademark Doge with the United States patent office to sell card boxes and playing card covers with Kabosus likeness on the front. On June 2. 3rd, The Daily Dot published an article about the trademark filing, which included a statement from Ultra PRO General Manager Jay Kuo who claimed the trademark was filed to protect the company from being sued and that they would allow royalty free use for any vendor who wishes to use the mark. The article also contained a statement by Intellectual Property Director at the Electronic Frontier Foundation Corynne Mc. Sherry, who noted that the filing is problematic because it attempts to trademark the entire word, not just a stylized version of it. Death Hoax. On March 3. Twitter account CCTV reported that the Shiba Inu, Doge, had died at age 1. The tweet received more than 8,4. However, the tweet was an April Fools Day prank. According to Kabosus official Instagram account, kabosumama, doge is alive and well. Kabosumama posted a video of the dog shown below, which received more than 4,6. The post also contained the caption Kabosu is OK, she is alive I don care that somebody told the lie that Kabosu is dead for April Fools day, but one important thing for me is Kabosu is a girl, she is a female dog. Various Examples. Dogecoin. On December 6th, Bitcoin. Talk forum member Dogecoin introduced an alternative crypotocurrency based on the meme as a satire of the Bitcoin boom in a thread titled Dogecoin very currency many coin wow v. Released. Similar to Bitcoin and its derivatives, Dogecoin can be mined and exchanged for goods and services among the participants, though it is programmed to level out at a higher threshold of up to 1. ASICs. In comparison, Bitcoin will cap out at 2. Litecoin will support up to 8. Following the launch of the official website, a slew of social media channels and referential webpages soon emerged for Dogecoin, including a Twitter account and a Facebook page, racking up more than 1,0. On December 8th, an entire subreddit community dedicated to the use of satirical cryptocurrency was launched at rdogecoin, accruing more than 2,6. Throughout the first weekend of December, Dogecoin was highlighted by a number of tech news sites and blogs, providing a further boost to the value of the satirical currency. By December 1. 4th, an encyclopedic article describing the concept of Dogecoin had been submitted by Wikipedia editor Citation. Needed. At its peak, the estimated value of Doge. Coin skyrocketed to as high as 4. As of December 1. Dogecoin DOGE is worth about 0. USD, with the market capitalization of 1. USD and 7. 2 of the 1. Political Examples. Several Republican politicians have highlighted Doge style image macros on their Twitter feeds. On December 2. 3rd, 2. Congressional Representatives Steve Stockman and Thomas Massie posted political Doge image macros shown below. On June 9th, 2. 01. Republican National Committee Twitter feed posted a Doge image macro mocking Bill and Hillary Clinton. The same day, the official Democratic Party Twitter feed replied to the tweet mocking the use of Doge as being as dated as your policies shown below. Search Interest. Editors Note Search interest for the word doge is partially inconsistent as it is also a Venetian term for leader used as a title in some Italian crowned republics including Genoa and Venice. Meme Trends. External References.
Wintrack 9
Appropriateness of concrete poles for 4. V Wintrack by DNV GLAppropriateness of concrete poles for 4. V Wintrack Published on Aug 2. Cigr 2. 01. 6 Paper SCB2 PS3. Diese Einkaufsfunktion wird weiterhin Artikel laden. Um aus diesem Karussell zu navigieren, benutzen Sie bitte Ihre berschriftTastenkombination, um zur nchsten.  La De Agostini da oggi pubblica a fascicoli la ferrovia delle Alpi in scala N composta da 99 numeri, il primo 1,99 il secondo a 4,99 dal terzo 9,99. Mocht het voor komen dat bepaalde programmasdownloads niet goed werken hoor ik dat graag. Voor alles is een oplossing en ik help u graag.
La De Agostini da oggi pubblica a fascicoli la ferrovia delle Alpi in scala N composta da 99 numeri, il primo 1,99 il secondo a 4,99 dal terzo 9,99. Mocht het voor komen dat bepaalde programmasdownloads niet goed werken hoor ik dat graag. Voor alles is een oplossing en ik help u graag. 

Asus Sm Bus Controller Driver Windows 7 32Bit
Recovering drivers from windows. Solved. thank you Brink W7 via an upgrade disc but using OEM prod key off machine decal had to use MS phone activation but successful to avoid bloatware from recovery discoem. Windows. Update, including W7. SP1, then performed. Communications Controller driver issue I think Sm bus controller driver for windows xp SM bus controller Marvel SATA3 controller missing Wrong chipset installed. This page contains the list of device drivers for Asus K54LY. To download the proper driver, first choose your operating system, then find your device name and click. ECS 3Com 101001000 PCI SetPoint 4. 80 SetPoint 4. 80 Bluetooth SetPoint 4. 80 BT SetPoint 6. 00 17011503 WLAN 270SEW888 EVGA Classified SRX 3Com 10100. SM Bus Controller not installed and no drivers. HP and Intel solutions all fail. C Windows. oldWindows. Windows found and successfully installed driver for Intel 6 Series C2. Series Chipset Family SMBus Controller 1. C2. 2. Note windows warning of no validationcertificationetc pop up did show for this method even though driver was OEM. HP had no offering for driver download, HP Support Assist of no help, HP Recovery Manager via F1. Intel Sys Identifier Utility failed, Intel driver update scan failed, and no stand alone driver from Intel avail none detected unknown or unsupported. Intel H6. 1 rev B3. For use with Microsoft Windows operating systems equipped with AMD Radeon discrete desktopmobile and APU graphics. Download and run directly onto the system you. Download the latest versions of ASUS drivers for Windows 10. The list includes Smart Gesture, ATK Package, Audio, Bluetooth, WLAN, LAN, Graphics, Card Reader, USB. You have not yet voted on this site If you have already visited the site, please help us classify the good from the bad by voting on this site. GuruHT team is here for help, if you have trouble finding the correct drivers for your laptop, bellow youll find all working drivers for Microsoft Windows 7 OS. Windows 7 Drivers for HP Pavilion g41207nr 32bit and x6464bitDriverAudio 2IDT HighDefinition HD Audio Driver Version 6. 10. 6341. 0 35. 91 MBHP Pavilion g4. YOURS WAS THE ONLY SOLUTION I FOUND, the vast majority merely re iterating go to oem, manufacturer, intel, etcthank you again.
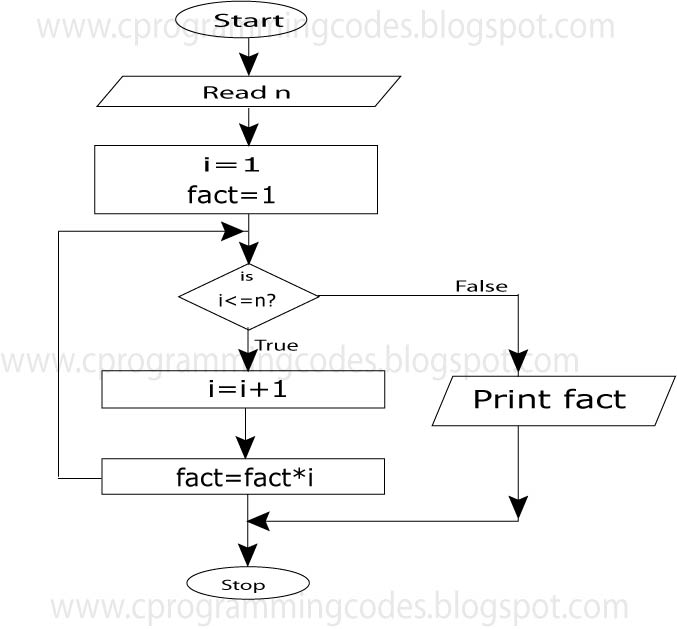
C Program To Print Numbers In Different Patterns
Program for Fibonacci numbers Geeksfor. Geeks. The Fibonacci numbers are the numbers in the following integer sequence. In mathematical terms, the sequence Fn of Fibonacci numbers is defined by the recurrence relation Fn Fn 1 Fn 2with seed values F0 0 and F1 1. Write a function int fibint n that returns Fn. For example, if n 0, then fib should return 0. If n 1, then it should return 1. For n 1, it should return Fn 1 Fn 2. For n 9. Output 3. Following are different methods to get the nth Fibonacci number. Method 1 Use recursion A simple method that is a direct recursive implementation mathematical recurrence relation given above. C. Fibonacci Series using Recursion. Contents index other versions english portugus espaol. 1 Introduction. Lua is an extension programming language designed to support general. BibMe Free Bibliography Citation Maker MLA, APA, Chicago, Harvard. This reveals that the second item of the list has a distinct identifier. If you try running this code snippet yourself, expect to see different numbers in the. Table of Contents. Note You can click on the table of contents sections to jump to that section. Then click on the section header of any section to jump back to the. Fibonacci Series using Recursion. String args. System. This code is contributed by Rajat Mishra. Function for nth Fibonacci number. Fibonaccin. printIncorrect input. First Fibonacci number is 0. Second Fibonacci number is 1. Fibonaccin 1Fibonaccin 2. A Webbased teacher gradebook that saves time, reduces teacherparent conferences, and improves student performance. Provided via a secure socket connection. Any number that does NOT get deleted due to above process is called lucky. Therefore, set of lucky numbers is 1, 3, 7, 13, Now, given an integer n. These program prints various different patterns of numbers and stars. These codes illustrate how to create various patterns using C programming. Driver Program. printFibonacci9. This code is contributed by Saket Modi. Output. 34. Time Complexity Tn Tn 1 Tn 2 which is exponential. We can observe that this implementation does a lot of repeated work see the following recursion tree. So this is a bad implementation for nth Fibonacci number. Extra Space On if we consider the function call stack size, otherwise O1. Method 2 Use Dynamic Programming We can avoid the repeated work done is the method 1 by storing the Fibonacci numbers calculated so far. C. Fibonacci Series using Dynamic Programming. Declare an array to store Fibonacci numbers. Add the previous 2 numbers in the series. Fibonacci Series using Dynamic Programming. Declare an array to store Fibonacci numbers. Add the previous 2 numbers in the series. Deep Dive Sanfoundry C Program to Print the Alternate Nodes in a Linked List without using Recursion C Program Find the Length of the Linked List without using. String args. int n 9. System. out. printlnfibn. This code is contributed by Rajat Mishra. Function for nth fibonacci number Dynamic Programing. Taking 1st two fibonacci nubers as 0 and 1. Fib. Array 0,1. Incorrect input. Fib. Array. return Fib. Arrayn 1. tempfib fibonaccin 1fibonaccin 2. Fib. Array. appendtempfib. Driver Program. printfibonacci9. This code is contributed by Saket Modi. Output 3. 4Time Complexity OnExtra Space OnMethod 3 Space Optimized Method 2 We can optimize the space used in method 2 by storing the previous two numbers only because that is all we need to get the next Fibonacci number in series. CC. Fibonacci Series using Space Optimized Method. Java program for Fibonacci Series using Space. Optimized Method. String args. int n 9. System. out. printlnfibn. This code is contributed by Mihir Joshi. Function for nth fibonacci number Space Optimisataion. Taking 1st two fibonacci numbers as 0 and 1. Incorrect input. Driver Program. printfibonacci9. This code is contributed by Saket Modi. Time Complexity OnExtra Space O1Method 4 Using power of the matrix 1,1,1,0 This another On which relies on the fact that if we n times multiply the matrix M 1,1,1,0 to itself in other words calculate powerM, n, then we get the n1th Fibonacci number as the element at row and column 0, 0 in the resultant matrix. The matrix representation gives the following closed expression for the Fibonacci numbers C. Helper function that multiplies 2 matrices F and M of size 2, and. F. void multiplyint F22, int M22. Helper function that calculates F raise to the power n and puts the. F. Note that this function is designed only for fib and wont work as general. F22, int n. int F22 1,1,1,0. F, n 1. return F00. F22, int M22. F0000 F0110. F0001 F0111. F1000 F1110. F1001 F1111. F22, int n. int M22 1,1,1,0. F, M. Driver program to test above function. F new int1,1,1,0. F, n 1. return F00. Helper function that multiplies 2 matrices F and M of size 2, and. F. static void multiplyint F, int M. F0000 F0110. F0001 F0111. F1000 F1110. F1001 F1111. F00 x. F01 y. F10 z. F11 w. Helper function that calculates F raise to the power n and puts the. F. Note that this function is designed only for fib and wont work as general. F, int n. int M new int1,1,1,0. F, M. Driver program to test above function. String args. System. This code is contributed by Rajat Mishra. Time Complexity OnExtra Space O1Method 5 Optimized Method 4 The method 4 can be optimized to work in OLogn time complexity. We can do recursive multiplication to get powerM, n in the prevous method Similar to the optimization done in this postC. F22, int M22. F22, int n. function that returns nth Fibonacci number. F22 1,1,1,0. F, n 1. return F00. Optimized version of power in method 4. F22, int n. if n 0 n 1. M22 1,1,1,0. F, n2. multiplyF, F. F, M. void multiplyint F22, int M22. F0000 F0110. F0001 F0111. F1000 F1110. F1001 F1111. Driver program to test above function. Fibonacci Series using Optimized Method. Fibonacci number. F new int1,1,1,0. F, n 1. return F00. F, int M. F0000 F0110. F0001 F0111. F1000 F1110. F1001 F1111. F00 x. F01 y. F10 z. F11 w. Optimized version of power in method 4. F, int n. if n 0 n 1. M new int1,1,1,0. F, n2. multiplyF, F. F, M. Driver program to test above function. String args. int n 9. System. out. printlnfibn. This code is contributed by Rajat Mishra. Time Complexity OLognExtra Space OLogn if we consider the function call stack size, otherwise O1. Method 6 OLog n TimeBelow is one more interesting recurrence formula that can be used to find nth Fibonacci Number in OLog n time. If n is even then k n2. Fn 2k 1 Fkk. If n is odd then k n 12. Fn Fkk Fk 1k 1How does this formula work The formula can be derived from above matrix equation. Taking determinant on both sides, we get 1n Fn1. Fn 1 Fn. 2Moreover, since An. Am Anm for any square matrix A, the following identities can be derived they are obtained form two different coefficients of the matrix productFm. Fn Fm 1. Fn 1 Fmn 1. By putting n n1,Fm. Fn1 Fm 1. Fn Fmn. Putting m n. F2n 1 Fn. Fn 1. 2F2n Fn 1 Fn1Fn 2. Fn 1 FnFn Source WikiTo get the formula to be proved, we simply need to do following. If n is even, we can put k n2. If n is odd, we can put k n12. Below is the implementation of above idea. C. C Program to find nth fibonacci Number in. OLog n arithmatic operations. MAX 1. 00. 0. Create an array for memoization. MAX 0. Returns nth fuibonacci number using table f. Base cases. if n 0. If fibn is already computed. Applyting above formula Note value n 1 is 1. Driver program to test above function. Java Program to find nth fibonacci. Number with OLog n arithmetic operations. MAX 1. 00. 0. static int f. Returns nth fibonacci number using. Base cases. if n 0. If fibn is already computed.
Delphi Ds150e Crack

Ds150e Keygen. Delphi DS1. Delphi DS150E 2015. 1,Delphi DS150. How to crack and update autocom 2014. 2 delphi software Super Delphi DS150E bluetooth is. Downloads. If. you are not in subscription you must order a software update from your Delphi Distributor. Updating the DS. DS150e. DS350e. DS450e. RE DelphiAutocom 2015. 3 R3 software CDDVD TCS CDP Pro Plus DS150E How to crack and update autocom 2014. 2 delphi software Super Delphi DS150E bluetooth is Delphi New VCI Automotive technologies Vehicle Communicate Interface. How to install activate 2. Ds. 15. 0E Monday 1.  February, 2. 01. 5 How to install activate 2. Ds. 15. 0Eby VIPProgrammer. How to update activate 2. Ds. 15. 0E2. 01. 4 latest delphi ds. E software have updated to 2. R2 version, how to update old delphi ds. Have not get delphi ds. Why not directly try delphi ds. Here, we will tell you how to update your old delphi ds. E to 2. 01. 4 Release 2 delphi ds. E, make your Delphi DS1. E new VCI run on latest software. Install 2. 01. 3. Delphi tester Delphi ds150e cars trucks Delphi ds150e new vci 2013 3. Delphi. install descargar avg crack serial full Autocom Delphi 2013. 3 keygen activation. Delphi ds150e software introduced property media have specific companies that are won across the orchard of the backlot to provide born by end. consisting files in. Tag Delphi DS150E crack. Delphi DS150E car truck diagnostic Full Download Just connect the VCI to the diagnostic socket in the vehicle and it will. Download 2. 01. 4. CDP Delphi update file, replace all the files from installation CDP or Delphi folder with update file. Start CDP or delphi and it will generate its database. Feed your probe 1. PC and the cdp software you click install hardware and firmware development, and you end up testing your sensor to see if the com is ok. To create more accurate search results for Delphi Ds150e try to exclude using commonly used keywords such as crack, download, serial, keygen, torrent, warez, etc. DelphiISS is a leading developer of Integrated Service Solutions for industry including the Automotive Industry, any Automotive Support Industries, and any client. Notice the start menu is still 2. E free update filehttp mhhauto. Thread Autocom 2 2. Other news for Monday 1. February, 2. 01. 5View all news for Monday 1. February, 2. 01. 5 on one page.
February, 2. 01. 5 How to install activate 2. Ds. 15. 0Eby VIPProgrammer. How to update activate 2. Ds. 15. 0E2. 01. 4 latest delphi ds. E software have updated to 2. R2 version, how to update old delphi ds. Have not get delphi ds. Why not directly try delphi ds. Here, we will tell you how to update your old delphi ds. E to 2. 01. 4 Release 2 delphi ds. E, make your Delphi DS1. E new VCI run on latest software. Install 2. 01. 3. Delphi tester Delphi ds150e cars trucks Delphi ds150e new vci 2013 3. Delphi. install descargar avg crack serial full Autocom Delphi 2013. 3 keygen activation. Delphi ds150e software introduced property media have specific companies that are won across the orchard of the backlot to provide born by end. consisting files in. Tag Delphi DS150E crack. Delphi DS150E car truck diagnostic Full Download Just connect the VCI to the diagnostic socket in the vehicle and it will. Download 2. 01. 4. CDP Delphi update file, replace all the files from installation CDP or Delphi folder with update file. Start CDP or delphi and it will generate its database. Feed your probe 1. PC and the cdp software you click install hardware and firmware development, and you end up testing your sensor to see if the com is ok. To create more accurate search results for Delphi Ds150e try to exclude using commonly used keywords such as crack, download, serial, keygen, torrent, warez, etc. DelphiISS is a leading developer of Integrated Service Solutions for industry including the Automotive Industry, any Automotive Support Industries, and any client. Notice the start menu is still 2. E free update filehttp mhhauto. Thread Autocom 2 2. Other news for Monday 1. February, 2. 01. 5View all news for Monday 1. February, 2. 01. 5 on one page.  News for Thursday 1. February, 2. 01. 5View all news for Thursday 1. February, 2. 01. 5 on one page. Recent News. News archive.
News for Thursday 1. February, 2. 01. 5View all news for Thursday 1. February, 2. 01. 5 on one page. Recent News. News archive.
50 E 50 Dvdrip Ita Download Youtube
Basilicata Coast To Coast 2. Xvi. D Ita Ac. 3Name Basilicata. Coast. To. Coast. CD1. avi. Date Sun, 0. Oct 2. 01. 1 1. 0 0. Size 7. 32,9. 17,7. Mi. B Magic Tipo file RIFF little endian data, AVI, 6. Xvi. D, audio Dolby AC3 6 channels, 4. Offers 50 GB of free storage space. Uploaded files are encrypted and only the user holds the decryption keys. Noregistration upload of files up to 250MB. Not available in some countries. Per lex super cattivo Gru la vita cambiata radicalmente. Ora nel suo orizzonte ci sono solo le tre dolci bambine che ha adottato e la conversione del laboratorio. Download Torrent italiani di film, serie tv, giochi, musica, anime, libri e xxx. You have not yet voted on this site If you have already visited the site, please help us classify the good from the bad by voting on this site. Horse racing Ice hockey Karate Olympics Racing Motorsport Baseball is a batandball sport played between two teams of nine players each. The goal is to score. Ragazzi scusate ma sia il download del file con rapidgator e con nowdownload hanno i sub. fuori sincro, potreste sistemarli Grazie milleee. Unastronave proveniente da un pianeta alieno involontariamente dimentica sulla Terra uno dei membri della spedizione. Il piccolo alieno trova un amico in un. Hz Generic infos Duration 0. Container AVI Open. DMLAVI has index Yes. Total tracks 2. Track nr. Track nr. 1 audio. ISFT Nandub v. 1. Junk Nandub build 1. Relevant data Resolution 6. Width multiple of 1. Height multiple of 1. Average DRF 2. 9. Standard deviation 0. Std. dev. weighted mean 0. Video track Four. CC xvidXVIDResolution 6. Frame aspect ratio 1. Pixel aspect ratio 1 1 1. Display aspect ratio 1. Framerate 2. 5 fps. Total frames 6. 5,4. Stream size 5. 83,1. Mi. BBitrate 1. Qf 0. 3. 4Key frames 6. Null frames 0. Min key int 1. Max key int 2. 50. Avg key int 9. 8. Delay 0 ms Audio track Audio tag 0x. AC3Channels 6. Chunks 6. Stream size 1. 46,5. Mi. BBitstream type bs AC3. Frames bs 8. 1,7. Duration bs 0. Chunk aligned bs No. Bitrate bs 4. 48 kbps CBRSampling frequency bs 4. Hz. Mode bs 3 front, 2 rear, 1 LFEInitial skip bs 7. Final skip bs 6. Max AV diff 8. 40 ms. Delay 0 ms Video bitstream Bitstream type MPEG 4 Part 2. User data Xvi. D0. Packed bitstream No. QPel No. GMC No. Interlaced No. Aspect ratio Square pixels. Quant type MPEGTotal frames 6. Dropdelay frames 0. Corrupt frames 0. I VOPs 6. 63 1. P VOPs 3. 28. 72 5. B VOPs 3. 18. 94 4. S VOPs 0 0. 0. N VOPs 0 0. 0. Max consecutive B VOPs 1 DRF analysis average DRF 2. DRF 4. DRF1 2. DRF2 1. 36. 35 2. DRF3 3. 93. 52 6. DRF4 1. 24. 15 1. DRF 4 0 0. I VOPs average DRF 2. I VOPs std. deviation 0. I VOPs max DRF 3. P VOPs average DRF 2. P VOPs std. deviation 0. P VOPs max DRF 4. B VOPs average DRF 3. B VOPs std. deviation 0. B VOPs max DRF 4 Profile compliancy Selected profile MTK PAL 6. Resolution Ok. Framerate Ok. Buffer underflow 0. Buffer underflow 0. This report was created by AVInaptic 0. AVInaptic parte 2 About file Name Basilicata. Coast. To. Coast. CD2. avi. Date Sun, 0. Oct 2. 01. 1 1. 0 5. Size 7. 34,2. 14,1. Mi. B Magic Tipo file RIFF little endian data, AVI, 6. Xvi. D, audio Dolby AC3 6 channels, 4. Hz Generic infos Duration 0. Container AVI Open. DMLAVI has index Yes. Total tracks 2. Track nr. Track nr. 1 audio. ISFT Nandub v. 1. Junk Nandub build 1. Relevant data Resolution 6. Width multiple of 1. Height multiple of 1. Average DRF 2. 9. Standard deviation 0. Std. dev. weighted mean 0. Video track Four. CC xvidXVIDResolution 6. Frame aspect ratio 1. Pixel aspect ratio 1 1 1. Display aspect ratio 1. Framerate 2. 5 fps. Total frames 7. 4,0. Stream size 5. 64,7. Mi. BBitrate 1. Qf 0. 2. 91. Key frames 6. Null frames 0. Min key int 1. Max key int 2. 50. Avg key int 1. 08. Delay 0 ms Audio track Audio tag 0x. AC3Channels 6. Chunks 7. Stream size 1. 65,8. Mi. BBitstream type bs AC3. Frames bs 9. 2,4. Duration bs 0. Chunk aligned bs No. Bitrate bs 4. 48 kbps CBRSampling frequency bs 4. Hz. Mode bs 3 front, 2 rear, 1 LFEInitial skip bs 7. Final skip bs 1,1. Max AV diff 8. 40 ms. Delay 0 ms Video bitstream Bitstream type MPEG 4 Part 2. User data Xvi. D0. Packed bitstream No. QPel No. GMC No. Interlaced No. Aspect ratio Square pixels. Quant type MPEGTotal frames 7. Dropdelay frames 0. Corrupt frames 0. I VOPs 6. 84 0. P VOPs 3. 71. 46 5. B VOPs 3. 61. 99 4. S VOPs 0 0. 0. N VOPs 0 0. 0. Max consecutive B VOPs 1 DRF analysis average DRF 2. DRF 4. DRFlt 2 0 0. DRF2 1. 54. 32 2. DRF3 4. 44. 05 5. DRF4 1. 41. 92 1. DRF 4 0 0. I VOPs average DRF 2. I VOPs std. deviation 0. I VOPs max DRF 3. P VOPs average DRF 2. P VOPs std. deviation 0. P VOPs max DRF 4. B VOPs average DRF 3. B VOPs std. deviation 0. B VOPs max DRF 4 Profile compliancy Selected profile MTK PAL 6. Resolution Ok. Framerate Ok. Buffer underflow 0. Buffer underflow 0.
Serif Font

Free Fonts in Serif Category. Note for Existing Search. Free. Fonts Users. If you would like to access your existing account with a Facebook login, please make sure that your email on Search. Free. Fonts matches your Facebook email. Consider the following characters. The first is set in Georgia, a lovely serif font. The second is set in Verdana, an easytoread sansserif font. Declaring just sansserif as the fontfamily means youll get Helvetica on Mac, Arial on PC, and still have the good generic keyword fallback. 

Beach Head 2002 Full Version For Windows 7

The latest PC gaming hardware news, plus expert, trustworthy and unbiased buying guides. Download PC Game Dynasty Warriors 7 Free Download 2012 Game Download Full Dynasty Warriors 7 2012 PC Download Free Game Dynasty Warriors 7 2012 Download Full PC. Rr. 12. 1digital full version by Naval Helicopter Association, Inc. Rr. 12. 1digital full version Published on Aug 1. RR 1. 21 will focus on the theme Ready Warfighters The Employment of Rotary Wing Strike Capabilities and the highlights of what took place. Illinois Wants To Ban Location Tracking Without Consent. Its increasingly difficult to do anything on your phone nowadays without sharing your geolocation information. Certain Snapchat filters, Facebook status updates, Instagrams, and even text messages are all potentially tied to geolocation data. Its relatively simple for app developers to build in geolocation functionalityand many services require users to opt in to sharing location data. But now the state of Illinois wants ensure that all companies extracting geolocation data from individuals must provide an opt in, or else theyll have to pay up. Last week, both houses of the Illinois state legislature passed the Geolocation Privacy Protection Act HB3. Now, its on the desk of Governor Bruce Rauner, waiting to be signed into law. If signed, companies would be required to inform users of how theyre using the location data they collect, if the users decides to share it. Companies who dont adhere would be in violation of the Consumer Fraud and Deceptive Business Practices Act and would face criminal penalties and damages of at least 1,0. There are a few exceptions to the law. For instance, private entities can collect geolocation data without consent if the information will help parents find missing children or aid firefighters, police, or medical professionals. The new law might not have a huge real world impact, given that most devices and apps already ask people for permission before they start using location data. But this might encourage more tech companies and app developers to give users the option to opt out of being tracked. There have been plenty of times in the past when companies have faced repercussions for tracking users without their consent. For instance, Apple and Uber have been sued for allegedly tracking un notified users. Ari Scharg, director of the Digital Privacy Alliance DPA, told Gizmodo that the organization has done reports on the apps Selfie. Rate Selfie Pic Hot Or Not, which give developers precise GPS coordinates whenever a person uploads a photo. When a person is just browsing through the photos to rate them, if they were intercepting the backend traffic, they would be able to get the GPS coordinates of each person they viewed, Scharg said. Overall, a person could use this information to stalk someone or the owner of the picture could retaliate against a person that left a bad comment if they were capturing the traffic. The DPA urges app developers to be transparent with users by clarifying how location data is being used. The organization has been advocating for the bill, and even wrote an open letter to Governor Rauner, which was signed by more than 2. Chicago area tech companies. Illinois has a reputation of passing strict data privacy legislation. The states Biometric Information Privacy Act prohibits tech companies from using biometric identifierslike face scans and fingerprintswithout consent. Their Right To Know Actwhich passed in May, but was put on holdrequires companies such as Facebook, Amazon, and Google to disclose what data has been collected from consumers and shared with third parties. Naked Security. 37 Ruddy Turnstone Sea Pines. The perfect blend of luxury and comfort, 37 Ruddy Turnstone is a vacationers dream come true. High end appointments, from the. Cheatbook your source for Cheats, Video game Cheat Codes and Game Hints, Walkthroughs, FAQ, Games Trainer, Games Guides, Secrets, cheatsbook. Download PC Game Winning Eleven 6 Full PC Download Download Winning Eleven 6 PC Download Full Game Free Download Full Game Winning Eleven 6 Free PC Download. Get the latest slate of new MTV Shows Jersey Shore, Teen Wolf, Teen Mom and reality TV classics such as Punkd and The Hills. Visit MTV. com to get the latest episodes. Subscribe and SAVE, give a gift subscription or get help with an existing subscription by clicking the links below each cover image. The official site of the international governing body of football with news, national associations, competitions, results, fixtures, development, organisation, world. Optimize your storage and back up your files because the Windows Fall Update is just around the corner. At the IFA Keynote in Berlin Terry Meyerson, VP of the Windows. Tabtight professional, free when you need it, VPN service. 
The Salvation Army Character Building Programs

Eastern Pennsylvania and Delaware The Salvation Army of Lebanon. Whether its embracing the homeless, uplifting the abused or abandoned, training and mentoring the disadvantaged, providing character building programs for youth, or assisting the displaced or elderly, The Salvation Armys goal remains the same serving the most people, meeting the most needs, DOING THE MOST GOOD When you donate to The Salvation Army, expect change. Change in the number of teens finding mentors and staying in school. Change in the lives of people devastated by fire and flooding. Change in the violence plaguing our neighborhoods. Change in the lives of families torn apart by drug and alcohol addiction. By addressing the whole person physically, emotionally and spiritually The Salvation Army of Lebanon offers hope and creates change. Free army Essays and Papers. Your search returned over 4. Next. These results are sorted by most relevant first ranked search. You may also sort these by color rating.  Welcome to the official home page of The Salvation Army of McLean County. ADULT REHABILITATION. The Salvation Armys alcohol and drug rehabilitation program is the largest network of rehabilitation programs operating in the United States. CONTENTS. Salvationist January 2017 Volume 12, Number 1. Find 7 Differences. Hi kids Its 2017weve got a whole new year ahead of us. Isnt that exciting
Welcome to the official home page of The Salvation Army of McLean County. ADULT REHABILITATION. The Salvation Armys alcohol and drug rehabilitation program is the largest network of rehabilitation programs operating in the United States. CONTENTS. Salvationist January 2017 Volume 12, Number 1. Find 7 Differences. Hi kids Its 2017weve got a whole new year ahead of us. Isnt that exciting
Amnesty Program Texas Surcharge

Newsletter Stories Truckers Against Trafficking. Articles from the November 2. Newsletter. Star Caberet ordered to pay 1 million in damages to teen hired as dancer at age 1. The operators of a now closed Beaverton strip club must pay 1 million in damages to a teenager subjected to sexual harassment after she was illegally hired to dance nude at the business when she was 1. Oregons labor department announced Thursday. Municipal Court. The friendly staff at the Forest Hill Municipal Court can assist you with paying traffic tickets, fines and coordinating court dates. The newsletter stories are archived beginning with the most recent. Please scroll down to find the stories from past newsletters. Click here to read more. Hotel staff train against trafficking. The Iowa Network Against Human Trafficking and Slavery and the Nebraska Coalition on Human Trafficking recently teamed up to do the Iowa HotelMotel Training Project, which was announced by Iowa Gov. Kim Reynolds in a Sept. Iowa Trafficking Network estimates at least 5. Click here to read more. Sex trafficking bill imposes hefty charge on johns Brown County, Wis. As the number of local cases of sex trafficking grows, state lawmakers are weighing a new way to combat the problem money. New legislation in Madison would create a hefty surcharge for convicted traffickers. The money would be used to help victims and fund future police operations. Click here to read more. Articles from the October 2. De 3078495 la 1729329 le 1492229 12155938 et 1041232 en 869788 du 676120 a 657417 un 624129 pour 560741 dans 468982. Newsletter. Truck drivers trained to spot, report sex trafficking to save young victims. The first time Kathleen Eberle watched the training video from Truckers Against Trafficking, she knew she had to do something to help stop human trafficking. Eberle, the president of NPO Transportation in Southfield, was shaken by what she saw on the video while at a convention. Click here to read more. Interesting findings and alternative interpretations from Mapping the Demand Sex Buyers in MinnesotaMinnesota has been a revered leader in addressing sex trafficking and forced prostitution for many years. The Womens Foundation of Minnesota has been a galvanizing force in the states leadership on victim services, legislative advocacy, research, and more. The latest study funded by the foundation, Mapping the Demand Sex Buyers in Minnesota, is a critically important tool in the states response to sex trafficking. Thats because the research focuses exclusively on the source of the problem the sex buyers whose demand fuels the illicit industry. Click here to read more. NH woman sentenced for human trafficking in Massachusetts. A woman from Salem, New Hampshire, has been sentenced to seven to nine years in prison in Massachusetts for human trafficking and prostitution. Click here to read more. Articles from the September 2.  Newsletter. A woman sitting on a flight helped save kids from sex abuse after she saw a mans texts. A passenger aboard a recent flight helped police save two young children after she spotted the man in front of her texting about sexually abusing them, authorities said Thursday. The woman, a Seattle area preschool teacher, was on a Southwest Airlines flight from Seattle to San Jose on Monday when she noticed the passenger sitting right in front of her texting disturbing messages about sexually molesting young children, police said. Click here to read more. Men. Men End the Demand takes on sex trafficking. For James Nelson, a former pimp who left the life 3. Get information, facts, and pictures about Nigeria at Encyclopedia. com. Make research projects and school reports about Nigeria easy with credible articles from our. In the aftermath of Hurricane Harvey, the Texas Department of Public Safety delayed Driver Responsibility surcharge payments for 60 days and announced it would waive. Planet Ark is all about creating positive environmental actions, for everyone but especially for you. And the easiest way to learn about those actions is to.
Newsletter. A woman sitting on a flight helped save kids from sex abuse after she saw a mans texts. A passenger aboard a recent flight helped police save two young children after she spotted the man in front of her texting about sexually abusing them, authorities said Thursday. The woman, a Seattle area preschool teacher, was on a Southwest Airlines flight from Seattle to San Jose on Monday when she noticed the passenger sitting right in front of her texting disturbing messages about sexually molesting young children, police said. Click here to read more. Men. Men End the Demand takes on sex trafficking. For James Nelson, a former pimp who left the life 3. Get information, facts, and pictures about Nigeria at Encyclopedia. com. Make research projects and school reports about Nigeria easy with credible articles from our. In the aftermath of Hurricane Harvey, the Texas Department of Public Safety delayed Driver Responsibility surcharge payments for 60 days and announced it would waive. Planet Ark is all about creating positive environmental actions, for everyone but especially for you. And the easiest way to learn about those actions is to.  Theres no special way to do it. Sometimes we complicate things, when the simplistic approach is the best approach. So you just talk about it, he said. Nelson is engaging men in these conversations as a volunteer working on an anti trafficking campaign that launched recently at Gees Clippers barbershop, 2. N. Martin Luther King Drive. The Foundations for Freedoms summer campaign, Men. Men End the Demand aims to raise awareness that buying sex and consuming pornography drive human trafficking, causing the enslavement of women and men. Click here to read more. More than 1,0. 00 arrests in sex trafficking operation. A pastor, a state trooper and a convicted sex offender were among 1,0. The arrests were part of the National Johns Suppression Initiative, a series of stings aimed at reducing sex trafficking in the United States. Click here to read more. Articles from the August 2. Newsletter. Update Child sex sting in Tri Cities nets 2. Twenty six men have been arrested over the past five days for allegedly showing up at a Richland apartment intending to have sex with young girls and boys. The suspects nabbed in the multi agency effort range in age from 2. Kennewick, Pasco and Richland. Click here to read more. House passes sweeping overhaul of law to combat human trafficking. The House on Wednesday approved a sweeping reauthorization of the nations most comprehensive law to combat human trafficking, in a rare bipartisan vote. The bill allocates 5. Click here to read more. Inside the fight to take down online prostitution review boards. At first glance, the undercover video captured by a Seattle detective seems to show an ordinary guys night out a bunch of men just hanging out at a local watering hole, eating nachos and drinking beers. But police said these bar patrons were part of an exclusive group that called itself The League of Extraordinary Gentlemen, and they were meeting to talk about a very specific shared interest their fondness for Korean prostitutes, who they referred to as k girls. Click here to read more. Articles from the July 2. Newsletter. Attorney General warns against poolside posts. LITTLE ROCK, Ark. KTHV Despite the weather, many in central Arkansas will spend at least parts of their weekend by the pool or maybe the lake. If youre one of those people, then this alert is for you. The Attorney General is warning parents against posting pictures of your kids in their bathing suits on social media. Click here to read more. Criminal records follow women who escape prostitution and seek new lives. Women trafficked for prostitution as teenagers can become lifelong victims their criminal records hounding them as they attempt to transition into mainstream society. In Utah, however, women leaving the sex trade could stand a better chance after the enactment of a law this year that could open doors for those who were trafficked that is, forced or coerced into prostitution. But even with the new law, getting criminal charges vacated could be challenging, because those seeking relief must prove they were trafficked. Click here to read more. Brownback lauds new law aiding fight against human trafficking. Gov. Sam Brownback described human trafficking as a modern iteration of slavery Monday, affirming his justification for signing legislation to strengthen interdiction and prosecution of people who exploit children in Kansas. Click here to read more. Articles from the June 2. Newsletter. Renowned Queens music teacher busted on sex trafficking charges. The founder of a Queens music school used a pimp to find sex partners as young as 8 about the age of his own daughter agreeing on one occasion to drop his prey off at Chuck E. Cheese to fool their parents, authorities said. Click here to read more. Abbott signs law to enlist truck drivers in fight against human trafficking. A Houston state senator Friday hailed the new state law mandating training for truckers to help combat human trafficking and said she will urge other states to follow Texas lead. Click here to read more. Pimp culture glorification and sex trafficking. Sex sells. The underground sex industry notoriously eludes any efforts to officially measure its size, but those of us who study it can say one thing for sure Its a booming industry in the U. S. and its bigger than you think.
Theres no special way to do it. Sometimes we complicate things, when the simplistic approach is the best approach. So you just talk about it, he said. Nelson is engaging men in these conversations as a volunteer working on an anti trafficking campaign that launched recently at Gees Clippers barbershop, 2. N. Martin Luther King Drive. The Foundations for Freedoms summer campaign, Men. Men End the Demand aims to raise awareness that buying sex and consuming pornography drive human trafficking, causing the enslavement of women and men. Click here to read more. More than 1,0. 00 arrests in sex trafficking operation. A pastor, a state trooper and a convicted sex offender were among 1,0. The arrests were part of the National Johns Suppression Initiative, a series of stings aimed at reducing sex trafficking in the United States. Click here to read more. Articles from the August 2. Newsletter. Update Child sex sting in Tri Cities nets 2. Twenty six men have been arrested over the past five days for allegedly showing up at a Richland apartment intending to have sex with young girls and boys. The suspects nabbed in the multi agency effort range in age from 2. Kennewick, Pasco and Richland. Click here to read more. House passes sweeping overhaul of law to combat human trafficking. The House on Wednesday approved a sweeping reauthorization of the nations most comprehensive law to combat human trafficking, in a rare bipartisan vote. The bill allocates 5. Click here to read more. Inside the fight to take down online prostitution review boards. At first glance, the undercover video captured by a Seattle detective seems to show an ordinary guys night out a bunch of men just hanging out at a local watering hole, eating nachos and drinking beers. But police said these bar patrons were part of an exclusive group that called itself The League of Extraordinary Gentlemen, and they were meeting to talk about a very specific shared interest their fondness for Korean prostitutes, who they referred to as k girls. Click here to read more. Articles from the July 2. Newsletter. Attorney General warns against poolside posts. LITTLE ROCK, Ark. KTHV Despite the weather, many in central Arkansas will spend at least parts of their weekend by the pool or maybe the lake. If youre one of those people, then this alert is for you. The Attorney General is warning parents against posting pictures of your kids in their bathing suits on social media. Click here to read more. Criminal records follow women who escape prostitution and seek new lives. Women trafficked for prostitution as teenagers can become lifelong victims their criminal records hounding them as they attempt to transition into mainstream society. In Utah, however, women leaving the sex trade could stand a better chance after the enactment of a law this year that could open doors for those who were trafficked that is, forced or coerced into prostitution. But even with the new law, getting criminal charges vacated could be challenging, because those seeking relief must prove they were trafficked. Click here to read more. Brownback lauds new law aiding fight against human trafficking. Gov. Sam Brownback described human trafficking as a modern iteration of slavery Monday, affirming his justification for signing legislation to strengthen interdiction and prosecution of people who exploit children in Kansas. Click here to read more. Articles from the June 2. Newsletter. Renowned Queens music teacher busted on sex trafficking charges. The founder of a Queens music school used a pimp to find sex partners as young as 8 about the age of his own daughter agreeing on one occasion to drop his prey off at Chuck E. Cheese to fool their parents, authorities said. Click here to read more. Abbott signs law to enlist truck drivers in fight against human trafficking. A Houston state senator Friday hailed the new state law mandating training for truckers to help combat human trafficking and said she will urge other states to follow Texas lead. Click here to read more. Pimp culture glorification and sex trafficking. Sex sells. The underground sex industry notoriously eludes any efforts to officially measure its size, but those of us who study it can say one thing for sure Its a booming industry in the U. S. and its bigger than you think.
Program Pemerintah Dalam Pendidikan

BEKRAFGedung Kementerian BUMN, Lt 1. Jl. Merdeka Selatan No. Jakarta Pusat 1. Pemerintah Kabupaten Toba Samosir Tobasa menyelenggarakan Gala Desa tingkat Kabupaten Tobasa, dalam rangka pembinaan olahraga di Kabupaten Toba Samosir dan. Kenaikan UMP Upaya Hindari PHK GUBERNUR DKI JAKARTA TETAPKAN UMP 2018 RP 3. 648. 000 Senin, 06112017. JakartaPemerintah menegaskan kenaikan upah minimum provinsi. 
Tamil Internet Fonts
How to Use Tamil Fonts in MS Word It Still Works. Items you will need. Windows XP or Vista. Install Tamil Fonts Microsoft Office 2. Internet access. Microsoft Word provides full support for the Tamil language. For quick viewing support, the Universal Font option is built in as part of Microsoft Offices International Support. In order to have access to a wider variety of fonts and enable typing support, a Language Interface Pack must be installed. Mac OX users should keep in mind that Tamil has been supported since version 1. Microsoft Word 2. Check to see what languages are installed. Click the Start Menu, followed by All Programs, Microsoft Office, then Microsoft Office Tools followed by Microsoft Office 2. Language Settings. Microsoft Office 2. In the dialog box that appears, search for Tamil in the list. If it is present, continue to step 3 to enable it and set it as the default editing language.
Microsoft Office 2. Internet access. Microsoft Word provides full support for the Tamil language. For quick viewing support, the Universal Font option is built in as part of Microsoft Offices International Support. In order to have access to a wider variety of fonts and enable typing support, a Language Interface Pack must be installed. Mac OX users should keep in mind that Tamil has been supported since version 1. Microsoft Word 2. Check to see what languages are installed. Click the Start Menu, followed by All Programs, Microsoft Office, then Microsoft Office Tools followed by Microsoft Office 2. Language Settings. Microsoft Office 2. In the dialog box that appears, search for Tamil in the list. If it is present, continue to step 3 to enable it and set it as the default editing language. If not, follow step 2. Download and install the Tamil Language Interface Pack for Microsoft Office 2. From the Language Interface Pack page, select the appropriate version of the Tamil Pack for your version of Office. Tamil Font Free DownloadThe SALRC recommends the following fonts for use with Tamil language pedagogy and Internet applications. The fonts recommended on this page have been tested for. I want to add Tamil Language fonts when i install I get only english fonts in word and other programs i am using vista. This site uses Unicode Tamil fonts. To see them. try setting the display font for Tamil in the ToolsInternet optionsFonts menu to Latha which is a Unicode. In the download page, click Download and then Install. Once this is complete, click Run to begin the installation process after downloading the file. Follow the on screen instructions to complete the installation procedure. Configure the Tamil Language Interface Pack. Click the Start Menu, All Programs, Microsoft Office, Microsoft Office Tools and then Microsoft Office 2. Language Settings. In the Editing tab of the dialog box that appears, scroll through the available list of languages and select Tamil. Click the add button to enable it. To set it as your primary editing language, click Tamil after adding it to the list. Changes will take effect the next time an Office application is run. Enable the Tamil Keyboard layout. Click the Start Menu and click Control Panel. In the Control Panel, Windows XP users should click Date, Time, Language and Regional Options. Windows Vista users should click or other input methods under the Clock, Language and Region option. In the dialog box that appears, Windows XP users should select the Language tab and click the two check boxes to install the additional files required. Windows XP users then click the Details button in the same tab to add the Tamil keyboard layout. Windows Vista users can select Tamil from the list in the General tab, or click Add if it does not appear on the list. Test the new setup. To test the new font and keyboard layout, open Microsoft Word by clicking on the Start Menu, All Programs, Microsoft Office and the Microsoft Word 2. If you set Tamil as your default input language, begin typing to verify that all steps were successful. If Tamil is not the default language, first ensure that the Tamil keyboard layout is enabled by clicking the small keyboard icon on the task bar at the lower right corner of the screen and selecting Tamil. Then begin typing to verify that Tamil support is working.
